As a security professional, you’re always on the lookout for insight on emerging security trends and for strategies to identify and control risk. A recent Top Security Threats Survey published by Securitas USA identifies and ranks the top threats and management issues facing corporate America. Please download as a reference companion to this article. Here, Pinkerton experts discuss the survey results, and share their insights on the topic, including emerging trends, the ever-changing risk landscape and how the top threats are interconnected. The overall feeling is that companies should be thinking more holistically as the world becomes increasingly connected.
Hazard & Event Risk — Workplace Violence Prevention/Response
John Lawrence, Vice President | LATAM (Latin America)
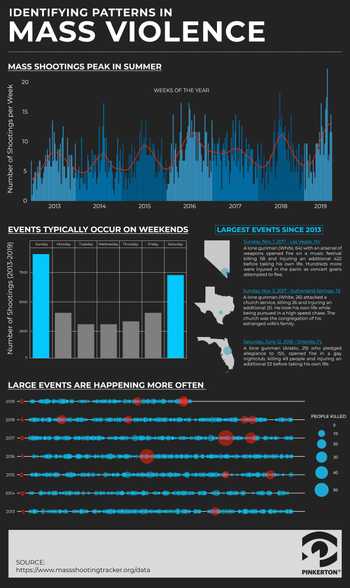
Workplace violence is often thought of as a physical attack. But it may also include threats, intimidation, and other disruptive behavior, oral or written statements, and gestures or expressions that communicate a direct or indirect threat of physical harm.
Warning signs are sometimes present; often people’s behaviors may be signs of potential workplace violence. Common indicators include intimidating behavior, such as argumentative exchanges, making direct or indirect threats, and sabotaging or stealing equipment.
Information regarding a threat of a harmful act — where you reasonably believe that the circumstances may lead to the act being carried out — should be reported immediately. Prevention begins with a process in place to report activities you may witness and/or observe. Reporting of violent acts or threats of violence to your immediate supervisor is imperative. How often have you heard after an incident occurred, “Oh yeah, he said something threatening to me once!” Identifying early warning signs and the reporting of any of these signs is an important part of prevention. Early warning signs may include excessive tardiness, excessive sick time, decreased production, and missing deadlines. Behavior such as overreacting to criticism or comments by peers, above normal levels of agitation, are also warning signs.
All employees should go through mandatory training on workplace violence prevention initiatives. This training can be conducted by trained HR representatives or outside resources that are qualified to provide the training. Supervisory personnel, especially in the HR arena, should have additional training to recognize the signs, and be able to refer potential problems to an Employee Assistance Program (EAP).
While “active shooter” incidents gain global media coverage, they are not as common as verbal and physical threats that occur in the workplace. Having sound physical security protocols in place, such as the use of access control badges and secondary barriers that make it more difficult for people to “piggyback” through a door (following someone who does have access) help prevent unauthorized personnel from gaining access to your facilities. One of the best prevention methods available for this problem is to have a comprehensive workplace violence program incorporated into employee orientation and training.
Operational & Physical Risk — Executive Protection (including travel security)
Richard Gurley, Vice President | Global Response Services
When providing executive security, assumptions like “today is like any other day” can be the mindset that opens the door to catastrophic impact. Providing executive security is not limited to what one knows or observes on any particular day, but is built upon the ability to gather pertinent information, plan, identify resources, conduct advances and have one absolute goal of “zero defect” in service delivery.
Operational execution no longer stands alone in providing security but must integrate reliable intelligence sources, technology (GPS Solutions), counter surveillance and real-time monitoring of social media. In a risk-based program of executive security, all quadrants of the risk wheel must be given consideration. A severe tropical storm from the Hazard and Event Risk quadrant not considered by the executive security team, could leave a CEO or key executive stranded — or even worse — exposed to potential harm. A confidential document detailing a new product left in a conference room that is not recovered during an after-meeting sweep by the executive security team, could represent a Technology and Informational Risk. Any breach in physical security, once identified by the media, can have a Market and Economic Risk.
These same risks discussed above must also be taken into consideration when providing security for all employees of a client, whether in their home/work locations or when traveling. Both the CEO and traveling employees must be briefed prior to travel in order to know the risks of a particular location, and how to react in the event of an incident.
Some clients with a significant global footprint have opted to have an entire Pinkerton Intelligence team embedded with them to provide both intelligence and business traveler support along with country risk reporting.
Operational & Physical Risk — Employee Selection & Screening
Jack Zahran, President
Cyber security and workplace violence remain right at the top of threat concerns for businesses. There are a variety of ways to reduce the level of threat, and thus better protect your organization from the identified security challenges. There is, however, a foundational component that should be addressed.
An initial and crucial step in creating a safer environment is to adapt a more comprehensive and diligent employee screening and selection process. In other words, reduce the possibility of dangerous individuals even getting their foot in the door of your company. A job candidate with a history of assaults, battery, and other violent incidents is not the type of individual your organization wants to be associated with at any level.
It is crucial to do complete criminal background checks so those type of candidates can be successfully filtered out of the list of prospects in your candidate pool. In addition, behavioral patterns that are not desired, or display a concerning pattern, will show up when doing a reference check. Documented aggression issues, argumentation with co-workers or superiors, and physical altercations will be uncovered in a detailed reference overview.
It is also imperative to identify any history of cybercrime or security breaches. Additionally, data perhaps not so blatant, but that displays the real possibility of concern along with the technical ability to potentially enact such breaches, should also raise a red flag – especially in the highly regulated industries like financial services.
There should also be consideration to launch a digital investigation of social media networks and other media sources that would display negative or questionable character issues of the job applicant. Civil investigations will show any previous theft or civil charges, along with other character concerns, and a professional psychometric assessment of the prospective employee can yield even more untrustworthy character traits that will help determine the bigger picture of the person being considered for the position.
It takes some company resources in time and labor intensity, but ultimately, this will be recouped by diminishing property loss and theft, and creating a safe working environment for your valued employees. Organizations are only as good as the employees on board, and to ensure that only the highest caliber people are employed, it is imperative that comprehensive employee screenings are always a top level priority, and that a definitive employee onboarding process is in place with no weak areas that can potentially be exploited.
Technology & Informational Risk — Intellectual Property/Brand Protection/Product Counterfeiting
Stephen Ward, Vice President | East Coast
In today’s interconnected world, Global Security teams are tasked time and time again to deal with issues that can affect the company’s reputation and brand. The threats to Intellectual Property and Brand Reputation can take many forms. For the purposes of this article, I will provide some insight on just a few that appear to cross the spectrum of companies.
One of the primarily areas of concern to global security teams at this time is addressing counterfeiting of corporate goods and the sales of these goods to the consumer. The first stop for any professional dealing with these issues is to be informed on the laws that protect their brand and where the goods are thought to be coming from. Identifying what departments are being affected can also assist in narrowing the scope of the investigation. Many times sales teams can advise where they are losing market share but still see the products being sold.
Find a global provider with boots on the ground and local knowledge so that they can conduct a concise and quick investigation into the actual threat and identify where the goods are emanating from. By using local agents that have ties to local law enforcement, the corporate security professional can leverage the local law enforcement connections in an effort to shut down the counterfeiters. Knowing what can and can’t be done in various regions is crucial to addressing this threat. Avoiding FCPA and UK anti-bribery issues are paramount in any investigation.
Education and the sharing of knowledge and forming coalitions are key. While many entities compete for market share and sales, they come together in the form of working groups to address and stem the flow of counterfeits. Competing pharmaceutical companies find that time and time again, they are faced with addressing the same counterfeiting threats that their competitors are facing. Sharing costs of investigations, when possible, is also a good practice. Leveraging your market weight as a group to move law enforcement and/or governments to take action is also a benefit from this type of collaboration.
Facing the threat in the virtual world is just as important as in the real world, with the understanding that protecting the company’s brand and reputation is also now one of the tasks of the security professional. Online policing and monitoring has also become a standard request at this time. We find that the improper use of a corporate logo and/or the impersonation of an entity on the web can negatively affect the company and its message.
As a corporate security professional, there are a number of tools that you can use to monitor the web internally. Knowing what is out there is key, as well as having the ability to shut down rogue sites, phishing and pharming sites, and remaining a step ahead of these online infringers. Using social media to advise the public of the threat posed by many of these phony websites can diffuse a situation where the company may be perceived as passive.
The threat to a company brand seems sometimes secondary than the physical threat. However, many times the fallout from a brand tarnishing event can follow a company for years and degrade all the goodwill the company has worked to build. While it has been said that imitation is the highest form of flattery, counterfeiting poses a real threat that can manifest in the form of safety violations and/or even death if not addressed. Education, action and collaboration are great tools that the security professional can call upon when addressing this threat.
Market & Economic Risk — Business Espionage/Theft of Trade Secrets
Brian McNary, Vice President | Global Risk Group
Business espionage is often confused with the plot for any of a dozen blockbuster films released in the last few years. Set aside worries of a brilliant megalomaniac sending squads of black-masked minions rappelling through skylights to whisk away your secret widget assembly guide; economic espionage is usually conducted more subtly, in often innocuous ways, and all too frequently accomplished without the victim’s immediate awareness. Let’s also set aside the worrisome number of corporations not clearly and effectively identifying information which requires protection, or do not provide the means of reporting suspicious activity – external or internal. Instead, it is important to look at the interconnectedness of the above concerns with the threat of trade secret loss and the compromise of business advantage by competitors.
Employee screening performed by a competent agency may well help you initially avoid a hiring error, but time passes and “life happens.” How well do you know the people trusted with your sensitive information? Have they been charged with illegal activity, suffered financial reversals or other personal changes which would disqualify them for the trusted positions they hold within your company? How would you know? When they travel internationally, do you fully and effectively prepare them for entrapment scenarios intended to compromise their values and co-opt them into acting in the interests of others? Could this leverage be the reason they loaded large amounts of proprietary data – or small amounts over time – onto a USB memory stick during that unusual Sunday morning they came in to work? Others seem to notice their somewhat “off” behavior, changes in personal interests or spending habits, increased interest in collaborating with other teams and willingness to volunteer for travel assignments. How do those who notice communicate these concerns, and why should they? As others respond – or seem to respond – to these behavioral changes, does the employee become agitated, easily angered, or prone to speaking of violent activities?
By now we should all be truly convinced that employee outreach and assistance programs are essential to creating and maintaining a safe workplace. According to the U.S. Bureau of Labor, in 2013 there were 397 fatal workplace injuries classified as homicides in the U.S., including suicides. We should also be cognizant of the fact that the most vulnerable links in our protective measures are the human ones, and have the awareness that there are nation states and competitors – not always different entities – hostile to your interests and willing to compromise your information systems by brute force or stratagem. Even aligned entities are abusing access to partner information.
Why should we be aware of this persistent and ever more sophisticated threat? Because the news is almost inescapable. PWC in 2014, in analyzing illicit economic activity in the U.S. and other advanced industrialized nations, estimated the economic impact of trade secret loss to equal between one and three percent of the U.S. GDP, at least $170, 000, 000, 000. In February of 2013, the White House released its Strategy on Mitigating the Theft of U.S. Trade Secrets.
Intellectual property must be protected, not merely for the benefit and reward of those who hold it, but for the continued growth of innovation. Theft of trade secrets and other forms of economic espionage have an impact barely estimable today, and of unknown consequence in decades ahead. Employees – the most vulnerable and essential part of any company – hold the keys to your market advantage today, and perhaps the very viability of your company in the future. It is vital that you seek to prepare them for overt and covert attempts to pry those keys from their hands. It is essential to have regular vetting for positions of trust, and crucial that your workforce understands its role in the protection of your shared future.